How to Manage IT Compliance Requirements in China
IT compliance in China is complex and requires a combination of legal and technical assessment due to a combination of factors. We discuss the major challenges, compliance requirements, and solutions for foreign businesses.
Companies with operations in China often find that they need to build and operate their own localized IT infrastructure or websites due to multiple reasons.
For example, slow international internet access has become one big obstacle for utilizing existing IT infrastructure outside of China to server the users or client in China. Building new IT infrastructure in China or speeding up the access to overseas systems is the popular solution on IT decision maker’s table.
Besides, with business process automation now an unstoppable trend in Asian countries, more and more companies operating in China are rapidly digitizing their financial, tax, and HR processes to transition to the far more productive and effective ways of administering their back office functions.
However, complex compliance requirements will prop up during the process, which needs a combination of legal and technical expertise to deal with.
IT compliance in China: What are the requirements?
China has in recent years continued to develop its cyber security regime by drafting, revising, and releasing relevant laws and regulations, resulting in a growing number of ever more complex and changing requirements in IT planning and compliance. Here we list some common compliance requirements that foreign companies must consider.
ICP filing
An Internet Content Provider (ICP) filing is a mandatory requirement for any website or system, which is to be publicly accessible through the internet in China, whether for internal or external use. It also covers the situation where CDN or other “proxy” servers are used to speed up the access to overseas sites. Without proper ICP filing, the internet service providers (ISPs) will block the access to the system or website.
ICP filing is supervised by the Ministry of Industry and Information Technology (MIIT) and the actual filing process is usually managed by the ISP or cloud service provider (CSP). It takes around one month to finish whole process.
Many foreign companies plan to deal with the ICP filing at the incorporation stage. Unfortunately, this is not feasible in practice because the authority in charge will ask the applicants to provide information, such as IP address, ISP name, domain certificate, etc. during the process, which can only be obtained after the relevant website has been built up and put into operation. Meanwhile, the supervising authority will access the website and review its content for judgement before the approval of ICP filing.
The suggested actions for ICP filing would be:
- Purchase the domain through MIIT authorized domain registrar and obtain the domain certificate;
- Engage with CSP and build the website (if selecting cloud option which is more common comparing to on-premise server option);
- Start ICP filing process with the information provided to the CSP (or ISP if using own on-premise server); and
- Add ICP filing number at the bottom of start page as evidence once obtaining the approval from MIIT.
PSB filing
In addition to an ICP filing, the Ministry of Public Security (MPS) requires a company to also go through a filing process with the local Public Security Bureau. This must usually be done within 30 days after an ICP filing has been made. Without the prompt filing, the PSB could again ask the ISP to shut down access to a system or a website, in addition to imposing a penalty on the company and / or technical staff who oversees the system.
The requirements and filing process are quite similar to that of the ICP filing. The whole process takes around one to two weeks.
ICP license
ICP license is a permit required for providing telecommunication services under specific circumstances, which has higher, more stringent requirements to meet, in terms of approval and compliance.
An ICP license is usually referred to as a B25 information service type permit. However, there is also the possibility of another type of permit needed, such as for B21 online data processing and transaction processing services.
The key point to judge whether an ICP license is needed is to confirm whether the website is “commercial” or not.
A type of analysis that should be conducted involves assessing the company’s business nature, business model, what kind of content will be showed in website, and what is the pathway adopted to interact with the user through the website. For example, allowing third-party vendors to do e-business on the company’s website will require an ICP license, but selling the company’s own product/service online and receiving money via Alipay or WeChat pay might not need the ICP license.
Considering that an ICP license is not applicable for wholly foreign owned enterprise, it is critical to do the analysis of ICP license’s applicability as early as possible when planning to enter into the China market. Foreign investors may need to find a Chinese partner if the ICP license does apply to their business model.
Data localization
As stipulated by the Cyber Security Law, the operator of a critical information infrastructure (CII) system shall store personal information and important data collected and generated during its operation within the territory of China. A prior approval is needed if the cross-border transfer of the above mentioned data is necessary. This can impose a major challenge to companies which utilize the existing IT system of their HQ.
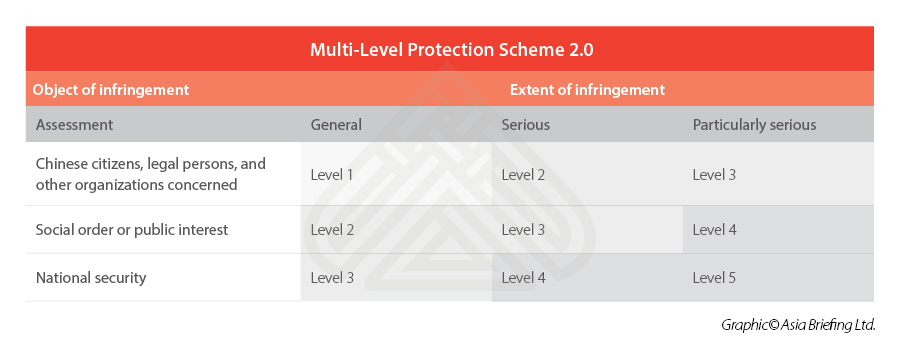
MLPS 2.0
The Multi-Level Protection Scheme (MLPS) is a set of national standards first introduced by China in 2004, then adopted into the Cyber Security Law (CSL) in 2017 and few national standards in 2019, and updated within what is now the MLPS 2.0 framework.
MPLS 2.0 gives more pressure to companies to maintain compliance, with five levels of regulated security protections. Level 1 is the least sensitive, while Level 5 is the most sensitive. Companies, as the network operators, are expected to verify their own systems to understand which of those levels they fall into, and which corresponding security control measures they are expected to adhere to.
For level 2 or above for example, an on-site evaluation of in-place security control measures must be performed by a government-designated “security auditing” firm.
Privacy
China has also paid increasing attention to personal information protection in recent years. Several campaigns were launched in 2019 to address the illegal collection of personal information in China, which spawned a range of standards that stipulate detailed requirements for privacy compliance.
Unlike Europe’s General Data Protection Regulation (GDPR) or California’s Consumer Privacy Act (CCPA), however, China does not yet have a single universal law on privacy so companies must refer to multiple regulations and instructions from different authorities.
China’s Personal Information Protection Law has just been included in the National People’s Congress’s 2020 legislative plan. Until this evolves, it will remain a significant challenge for companies operating in China which, for now, must refer to multiple regulations and instructions from different authorities, making compliance rather complex.
In March 2020, China released a new national standard on personal information, the GB/T35273-2020 Information Security Technology – Personal Information Security Specification (the Standard), which took effect on October 1, 2020.
Besides claiming that it holds similar principles like Europe’s General Data Protection Regulation (GDPR), the Standard gives a wider definition of personal information. For example, a wider scope of information is treated as sensitive personal information, which requires stronger protection, such as the financial information, the bank account information, the transaction and consumption records, etc.
Moreover, the Standard gives very specific requirements, such as defining how many mouse-clicks is allowed when users locate related privacy-related settings on website, the format and layout of privacy notice’s interface, etc.
Companies are suggested to pay attention to the new requirements imposed by the Standard.
WeChat ban
In the context of the escalated US-China trade tensions, the US administration issued an executive order in August to prohibit Americans and US firms from “any translation that is related to WeChat”, which was supposed to take effect starting from September 20, 2020.
Although this was blocked by a judge with a preliminary injunction on September 19 temporarily, it is time to seriously think of a “Plan B” for the US companies in China that use WeChat official accounts to promote their services or products.
A WeChat official account is not allowed to change the “account owner” directly. But simply abandoning this promotion channel that has a large size of fans is not a good idea, either. Luckily, the WeChat official account can be transferred to a different company owner with all history data, and more importantly, fans.
So, transferring the “ownership” of the WeChat official account to a trustworthy partner would be one suitable temporary option for keeping the channel live and meeting government’s request.
Some tips to manage compliance challenges
To deal with the IT compliance challenges, it is important to combine the forces of IT technical and legal expertise together within compliance processes. Pure legal advice often lacks practical input from genuine IT experience, and can be very hard to apply in the real world.
On the other hand, pure IT advisory tends to focus on the IT aspects and may have a low awareness or sensitivity to legal compliance requirements. Working with both technical and legal professionals would be the most suitable option.
With this concept in mind, the following approaches can help to mitigate the potential risk of cyber security and non-compliance:
1. Zero-trust strategy
Under a traditional security strategy, a security perimeter can be defined with users inside the perimeter designated as being within a “trust” zone. Any users in locations outside the perimeter are designated as being within the “distrust” zone.
The people or devices in the trust zone have looser security controls while any access from the distrust zone is controlled more strictly. However, in practice what tends to happen is that attacks from inside the trust zone have become more and more prevalent, with larger associated risks.
An alternative to this methodology is the zero-trust strategy, which means never trust anyone or any device by default. This approach is getting more and more popular to meet complex security challenges.
Each access from any device and any person at any location needs to be evaluated with multiple factors before access control is granted or declined. This is usually achieved with an artificial intelligence-based security control system.
2. Centralized platform with DLP and information protection
To meet the challenge regarding cyber security and compliance, one important suggestion is to implement one centralized platform, which covers all business needs, in which all business related data could be stored and managed under the control of the company.
Additionally, all data saved on devices (data at rest) should be encrypted, for example, enabling BitLocker encryption on laptop, in case the devices are lost at some point.
All data in transmission should be exchanged with secure protocols, such as HTTPS/TLS connection. Role-based access control (RBAC) and other access control methods should be applied for any data in use.
In addition, the company should consider deploying data loss prevention (DLP) measures to prevent sensitive business data being transferred out of the organization accidentally or intentionally. For very important data, further information protection measures, such as Azure information protection, should be considered and applied on a document level to expand the security control outside of the organization, wherever the document is.
One example of such a platform is the Microsoft365 platform, which combines email, file, message, meeting, and productivity tools to meet all business requirements, while all data is saved within the same platform with centralized control.
3. IAM protection
Identification and Access Management (IAM) protection is suggested to be used to provide stronger protection to user accounts, considering the most common and effective ways of user account attacks are through spoofing, trojans, and malwares.
One simple way to achieve this is to implement Multiple Factor Authentication (MFA) for user accounts, which can prevent the illegitimate access to systems even if the users’ account and password are compromised. It will be even better if the IAM solution is AI-based, such as the Azure AD Security, which can provide additional control for conditional access.
Finally, companies are also suggested to provide regular training to their staff to increase the security awareness as users are the final important defense line for security threats. An internal spoofing penetration check can be very helpful to identify the most vulnerable users, to be followed up with relevant training to those users on security awareness topics.
About Us
China Briefing is written and produced by Dezan Shira & Associates. The practice assists foreign investors into China and has done so since 1992 through offices in Beijing, Tianjin, Dalian, Qingdao, Shanghai, Hangzhou, Ningbo, Suzhou, Guangzhou, Dongguan, Zhongshan, Shenzhen, and Hong Kong. Please contact the firm for assistance in China at china@dezshira.com.
We also maintain offices assisting foreign investors in Vietnam, Indonesia, Singapore, The Philippines, Malaysia, Thailand, United States, and Italy, in addition to our practices in India and Russia and our trade research facilities along the Belt & Road Initiative.
- Previous Article Die führenden Trends im chinesischen Dienstleistungssektor nach der Beeinträchtigung durch COVID-19
- Next Article Shenzhen Announces Comprehensive Pilot Reforms Plan amid 40th SEZ Anniversary